Cyber Security Passwords
Many systems are protected by a simple password. This is not ideal as passwords can in many cases easily be broken, reused, or otherwise abused by attackers. This section will explore attacks and defenses regarding passwords.
Password Strength
What determines a strong password? Is it how complex the password is? How many characters it has? The number of special characters?
The famous comic creator xkcd.com brilliantly shows how passwords can be attacked in the comic below. Review it for a second and let us discuss further.
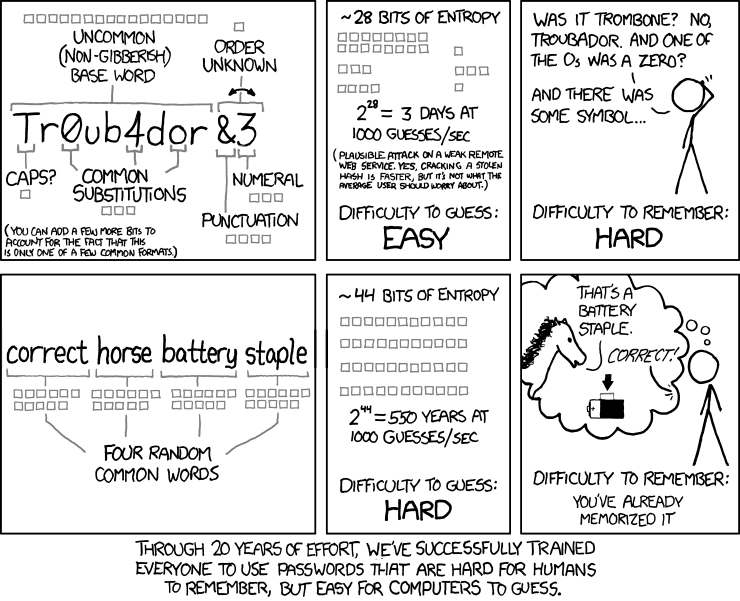
Comic from XKCD: https://xkcd.com/936/
If we consider the first password Tr0ub4dor&3, this password is will fit most password policy rules, for example having capitalized letter, numbers, special characters and a length of 11 characters. This password has however some problems, it is:
- Hard to remember. Did you replace the first o (the letter) character with a 0 (the number), or was it the second? Did you replace the a character with a 4, or not?
- Hard to type. You have to type in different letters, numbers and special characters in a special order. It will likely not be the fastest words being typed on your keyboard.
- It is not very strong! The password is based off a rather common word and it does not offer much strength, only about 28 bits of entropy.
Instead of selecting passwords which have these negative factors, we can instead greatly increase the entropy of passwords in simple ways. If we consider the password CorrectHorseBatteryStaple we see a considerate improvement of the password:
- The password is easy to type. Typing in regular words is for many an everyday activity and you can get really fast at it.
- It is easy to remember. By using a visual picture of the password, a horse, a battery, a staple and the word correct, we can remember it much easier.
- It is significantly stronger against most password cracking activities! It offers about 44 bits of entropy, making it really hard to crack.
Passwords like this one is called passphrases and is generally a much better practice than a simple word with some complexity. Consider how you could improve the password to be even stronger, and to fit password policy rules such as special characters and capital letters! You can even use spaces in your password, making passphrases even more natural to type.
Password Managers
Writing down your password has for many years been considered a bad-practice, but is it really? Using the same password across multiple services online has a significant risk, what if one of those platforms get hacked? Then that password is compromised and attackers can re-use the password across all other services where it is used.
To fight this problem, the recommendation is to not re-use the same password across multiple services. This makes it really hard for users as they are not only required to use unique passwords, but at the same time create strong and robust passwords! A password manager help solve this problem by offering users to, in a secure as possible way, write down passwords in a file, database or other system, making passwords easy accessible and ensuring they are strong and unique across different services.
When implemented correctly, a password manager will:
- Make the use of the Internet a much more secure activity
- Increase productivity as passwords for different services can easily be found, copied and pasted into the respective services the user want to log into
- Offer easy ways to reset and regenerate new passwords when needed.
Writing down passwords is considered a much lower risk for our users rather than having them reusing passwords. Yes, this is not a perfect solution as the password manager could potentially get compromised, however it is considered a much more safe approach.
Passwordless Solutions
What if passwords in themselves could be put to an end? There is always someone who can not type in a longer passphrase as their password every day. There may be several reasons for this, for example:
- Non IT savvy workers in the office
- A doctor who visits many different computers in the hospital, every day while visiting different patients in different rooms
- It is hard to type in the password on the system which requires it
The development and implementation of systems which does not require users to provide a password is developing rapidly. Instead of asking users to authenticate with a password, what if we allowed them to use for example:
- Something they are, for example their face or fingerprint
- Something they have, for example a token or their cell-phone
There are challenges to this, but in terms of security, are we really making the problem worse, or better for our users? We must remember we are not looking to implement perfect security systems, they are normally outside of reach and not implementable, so instead we must make careful considerations on how we can limit the threats and at the same time make life easier for our users. Passwords are not perfect, and neither is passwordless solutions. Which one will you implement for your users?
Multi-Factor Authentication
As we learn that regardless of what solution is used to verify users, there will still be significant risks associated with their accounts, other solutions can be implemented to help reduce the risk.
Multi-Factor Authentication allows solutions to not only verify a user based on for example their password, but at the same time require the users to present a second factor to prove who they are.

There can be several different ways to ask for a second factor. Here are a few examples:
- Use an authentication application on a smart-phone to provide a secret code
- Receive a secret code via SMS ("Short Message Service") on a phone
- Use a hardware token to provide a secret code
- Present a fingerprint or face to identify the individual
All of the above requires not only a password to be known, but also asks for a second item (a factor) to be provided.
Solutions like these are sometimes considered very invasive to the users. To help solve this problem a concept of DAC ("Discretionary Access Control") can be applied. DAC allows the login solution to consider whether or not to challenge a user with a multi-factor code. For example a multi-factor might only be necessary when a user:
- Logs in from a new location
- Uses a different browser or software to access the application
- Tries to perform a sensitive action in the application, for example change password or perform a money transaction above a certain threshold
Password Guessing
When attackers encounter applications and services, there might be the opportunity to do Password Guessing. Password Guessing is an activity which involves attackers interacting with the application over the network, trying lists of different combinations of usernames and passwords.
Password Guessing gives the attacker an opportunity to find accounts with a weak username and password combination.
If the attacker is successful in finding a valid account to log in with, new opportunities is presented to the attacker. Consider what kind of functionality and data is now presented to the attacker. Here are some examples where and attacker successfully guesses someone's password:
- Attacker accesses an email account of an employee. Inside there are thousands of emails ranging years back in history. Within the emails there are passwords communicated, allowing attacker to log into more systems. Furthermore, hundreds of attachments are present, some which may contain very sensitive information.
- Attackers successfully guess the Admin accounts password for an HVAC ("Heating, Ventilation and Air Conditioning") system whos responsibility is to cool down the server room. The attackers are able to change the parameters of the HVAC and through careful modification causes the server-room to overheat.
- A VPN service is available on the Internet, allowing employees to reach internal resources. One of the employees has a weak password which is guessed by an attacker through days of repeated password guessing. The attacker accesses the VPN service and is now on the inside network of the organization. From here, the attacker installs ransomware within the organization.
- A web application is deployed on the Internet. It holds no obvious vulnerabilities from the outside, however attackers were able password guess into a regular users account on the system. Because the company hosting the web application trusts their users, the web security on the inside of the application was poor. From here, the attacker was able to use web exploits to compromise the server.
Many network services have built-in administrator accounts, some even with the default password unchanged since it was installed. For each service on the network, attackers can try to log in with default credentials. Furthermore, the attacker can try typical and weak passwords. Here are some examples of typical and weak passwords. Notice all of them end with an exclamation mark in order to defeat password policies:
| Password | Comment |
|---|---|
| Summer2021! | Many people, including helpdesks of companies, perform password resets and set the password to the season of the year and the year we are currently in. |
| W3schools123! | The name of the company is often used as peoples passwords. The number 123 and ! at the end is selected by users to pass password policies and make it a bit more complex. |
| Rosalynn2006! | Rosalynn, perhaps someone's child? Users often use something of personal affection as their passwords. Names of children and perhaps the year they were born is very popular. |
| Qwerty123456! | A seemingly random password? This password is someone pressing keyboard keys in order, then using numbers to do the same thing. |
A tool which allows us to easily configure lists of usernames and passwords to try against a multitude of different services is THC-Hydra (https://github.com/vanhauser-thc/thc-hydra). It supports plentiful of protocols to attack such as:
- RDP ("Remote Desktop Protocol")
- FTP ("File Transfer Protocol")
- SMB ("Server Message Block")
- Telnet
- SSH ("Secure Sockets Host")
To use THC-Hydra to target for example FTP, the following command can be used:
hydra -L common_usernames.txt -P common_passwords.txt ftp://localhost/
This command uses a list of common usernames and common passwords to try each of them against the FTP service at localhost or an IP address of your choice.
Credential Stuffing
A common attack for attackers to use is Credential Stuffing. This involves attackers downloading huge databases of credentials and testing applicable credentials against the network service. A leak of credentials happen when a third party service is hacked, database is stolen and then leaked on the Internet for anyone to download.
Unfortunately many users re-use the same password on different services, allowing Credential Stuffing attacks to become very efficient against organizations.
Password Cracking
While Password Guessing is an online attack, Password Cracking is an offline attack. It involves attackers stealing password representations from a target first.
Passwords are typically represented as a password hash. A hash is way to store users passwords by sending them through a one-way function, making the password impossible to reverse unless password cracking is used.
If the attacker is capable of retrieving credentials from a system, these credentials are likely to be protected via encryption or hashing. Hashing is a one-way function designed to not be reversed into its original value.
Password cracking involves using computing power, that is the CPU ("Central Processing Unit") and GPU ("Graphical Processing Unit"), to try create password guesses which matches the protected credentials retrieved from the system.
Services Without Authentication
By exploring and discovering applications sometimes you can encounter applications which are not protected with authentication. These applications are useful for attackers to explore, for example taking advantage of a search field hunting for sensitive information.
Many applications on a network can freely be explored, sometimes providing attackers with the exact date they are looking for.
When performing network mapping and port scanning exercises, each discovered system and service should be explored.
Using Existing Credentials
Typically an attacker is already using credentials of users in the environment. For example if an attacker has compromised someone's computer system they can re-use the credentials already in-use by the system.
This provides attackers with many more opportunities. Consider all the applications which could now be abused. For example:
- SharePoint
- HR and Accounting
- VPN ("Virtual Private Networking")
Once an attacker has access to an application behind access control, vulnerabilities and data is often plentiful.
Credentials from a system can also be extracted via different means, typically involving having administrator access of the system. Mimikatz (https://github.com/gentilkiwi/mimikatz) is such a tool which tries to dump the credentials from the system.
